Payday

Video Tutorial
Please wait for video to load...
Written Walkthrough
FOOTHOLD
Starting with an Namp scan we get the following ports open:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 4.6p1 Debian 5build1 (protocol 2.0)
80/tcp open http syn-ack ttl 61 Apache httpd 2.2.4 ((Ubuntu) PHP/5.2.3-1ubuntu6)
110/tcp open pop3 syn-ack ttl 61 Dovecot pop3d
139/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 3.X - 4.X (workgroup: MSHOME)
143/tcp open imap syn-ack ttl 61 Dovecot imapd
445/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 3.0.26a (workgroup: MSHOME)
993/tcp open ssl/imap syn-ack ttl 61 Dovecot imapd
995/tcp open ssl/pop3 syn-ack ttl 61 Dovecot pop3d
The two best services (in my opinion) to start our enumeration out of these ports are port 80 and port 445. For this writeup we will start with port 80. Visiting the web application we are greeted by a Internet Shop where you can purchase products and services related to technology.
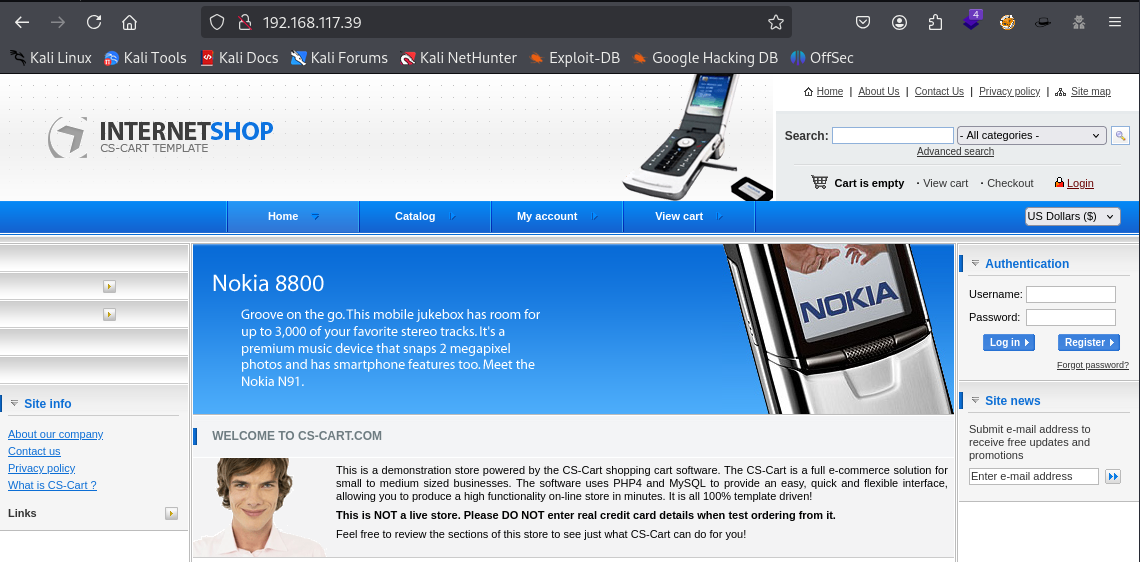
Trying default credentials of admin:admin we get logged in! Having a click around the application we don’t find anything immediately vulnerable. A search in google for “cs-cart exploit” gives the following result.
https://gist.github.com/momenbasel/ccb91523f86714edb96c871d4cf1d05c
This is an authenticated RCE exploit. Well that’s great because we are already authenticated as the admin user! This talks through step by step how to exploit this web application to get Remote Code Execution.
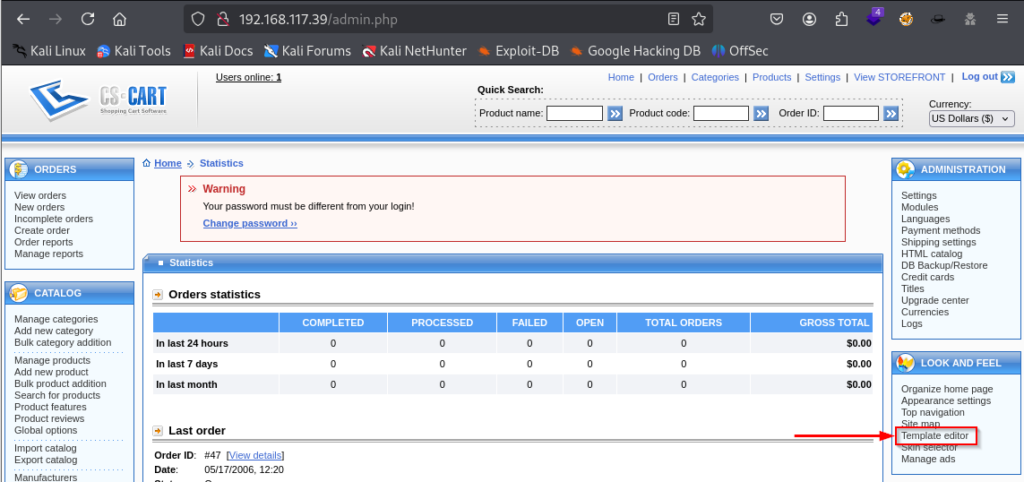
- Visit /admin.php (and log in if you havn’t already)
- Under the Look and Feel section, click on “template editor”
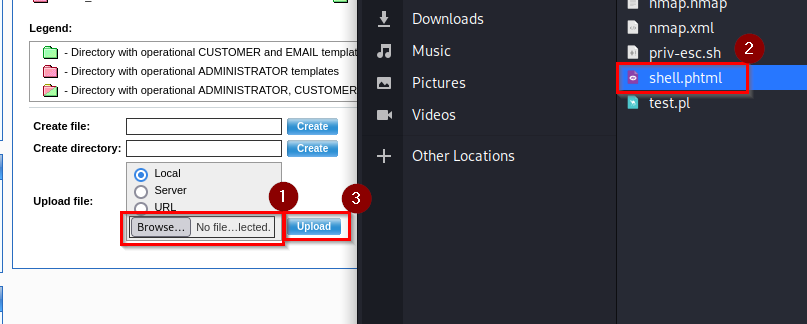
- Upload a malicious .php file, making sure you rename it to a .phtml file before you upload it.
- Once the file has been uploaded, visit the following to get a connection back to your listener http://<IP>/skins/shell.phtml
Okay great, so firstly we need log into the /admin.php page, and then click on “template editor”.
Then use a .php shell from pentestmonkey (make sure to change the IP and port in the code).
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
Then rename it to .phtml. Once that’s done, click the browse button, locate the file, then click the upload button.
Lastly, now the file is uploaded all you have to do is visit the following URL http://<IP>/skins/shell.phtml with a listener running.
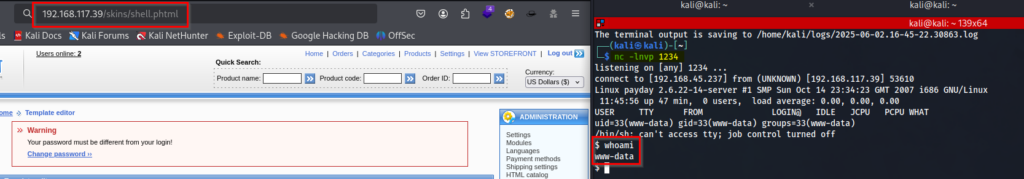
And we get a foothold on the box as “www-data”.
PRIVILEGE ESCALTION
Now I ran all my enumeration and tools and had gone through all of the potential misconfigurations I could identify and none of them worked. I did know from my enumeration there was a user on the box called “Patrick” and assumed we needed to move laterally over to that user. As a result of running out of ideas, I started trying default credentials for this user as a bit of a YOLO move. I felt frustration and relief at the same time when the credentials of partick:patrick actually worked and I now had a shell as the user patrick.
NOTE: You will probably need to upgrade your shell before running the “su patrick” command. This can be seen here https://blog.ropnop.com/upgrading-simple-shells-to-fully-interactive-ttys/. Scroll down to “Method 1: Python pty module”
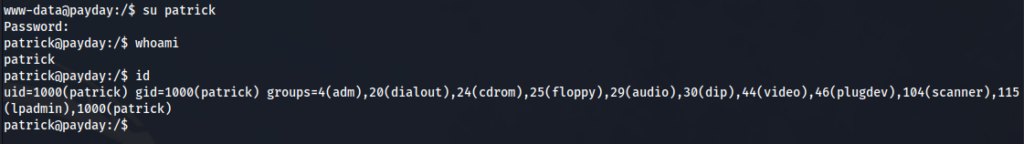
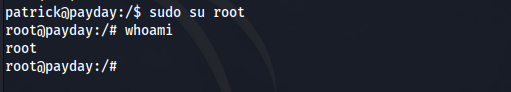
Now that we are the user Patrick we can start our enumeration all over again to see what this user can do. Running the “sudo –l“ command reveals privileges of sudo that patrick can run. We are able to run sudo -l because we now know that patricks password is “patrick”.
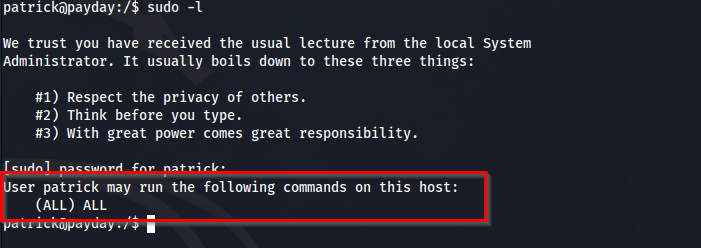
Well if you see this then it means GG. This is saying that the user patrick can run any command with sudo privileges without needing a password. Essentially you are root already, you just need to add sudo to any command. We use the su command again to swtich our user over to root.